Penetration Testing vs. Blue Team Defense: A Tactical Overview
In cybersecurity, two teams play a critical game of offense and defense. The Red Team simulates attacks by using penetration testing techniques to find vulnerabilities before real hackers do.
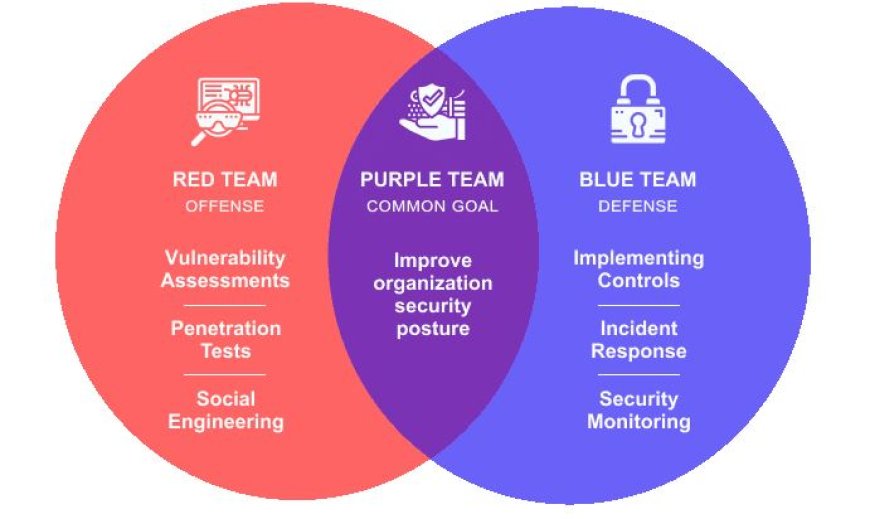
In the world of cybersecurity, one of the most effective ways to strengthen defenses is through a constant game of attack and defense; and that’s where the Red Team and Blue Team come in.
These two roles simulate real-world cyber conflict inside an organization to test and improve security. One mimics the adversary, while the other stands guard.
Red Team: The Ethical Offense
Red Team members act like real attackers. They simulate everything from phishing attempts to full-scale network breaches - legally and ethically - with one goal: find the holes before someone else does.
They use tools and tactics like:
- Penetration testing
- Exploiting misconfigurations
- Social engineering
- Vulnerability chaining
Their job isn't to break things for fun, it’s to expose weaknesses the organization might not even know exist.
Blue Team: The Silent Defenders
On the flip side, the Blue Team is responsible for defending the organization in real-time. They:
- Monitor systems for unusual activity
- Investigate alerts from SIEM tools
- Respond to incidents
- Strengthen network architecture
They are the last line of defense when an attack happens, and their feedback is crucial to improving both day-to-day security and long-term resilience.
Purple Teaming: Working Together
While Red and Blue teams have opposing roles, collaboration between the two (often called Purple Teaming) brings powerful results. The insights from both sides help organizations:
- Patch real weaknesses
- Improve detection and response
- Train staff for better awareness
Final Thought:
Understanding Red vs. Blue isn’t just for professionals in the field, it gives any organization insight into how cybersecurity is both proactive and reactive.
Building a strong defense starts with understanding how the offense thinks.
Social Snippet:
Red Team vs. Blue Team - see how offensive and defensive tactics work together to keep systems secure!
What's Your Reaction?
 Like
3
Like
3
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
1
Wow
1