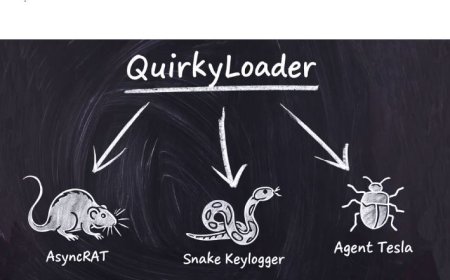
QuirkyLoader: The Malware Delivery Engine You Need to Watch
Joy Livingstone Aug 21, 2025 0 27

HR giant Workday says hackers stole personal data in recent breach
Joy Livingstone Aug 18, 2025 0 55

Microsoft Windows Vulnerability Exploited to Deploy PipeMagic RansomExx Malware
Joy Livingstone Aug 18, 2025 0 14

Malicious PyPI and npm Packages Discovered Exploiting Dependencies in Supply Chain Attacks
Joy Livingstone Aug 18, 2025 0 33

ERMAC V3.0 Banking Trojan Source Code Leak Exposes Full Malware Infrastructure
Joy Livingstone Aug 18, 2025 0 29
Mobile Phishers Target Brokerage Accounts in ‘Ramp and Dump’ Cashout Scheme
Joy Livingstone Aug 18, 2025 0 63

Norway spy chief blames Russian hackers for hijacking dam
Joy Livingstone Aug 15, 2025 0 52

Hackers Found Using CrossC2 to Expand Cobalt Strike Beacon’s Reach to Linux and macOS
Joy Livingstone Aug 15, 2025 0 57

Cisco Warns of CVSS 10.0 FMC RADIUS Flaw Allowing Remote Code Execution
Joy Livingstone Aug 15, 2025 0 16

QakBot Resurfaces in New Phishing Campaigns Post-Takedown
Joy Livingstone Aug 7, 2025 0 13

Understanding Data Privacy Regulations: What They Mean for You
Joy Livingstone Aug 5, 2025 0 16

How WannaCry Ransomware Spread Globally: A Malware Breakdown
Joy Livingstone Aug 5, 2025 0 97

Penetration Testing vs. Blue Team Defense: A Tactical Overview
Joy Livingstone Aug 5, 2025 0 62