When Employees Become the Weakest Link: Lessons from Insider Threats
Not all cybersecurity threats come from outside attackers. Insider threats, whether intentional or accidental, pose significant risks to organizations.
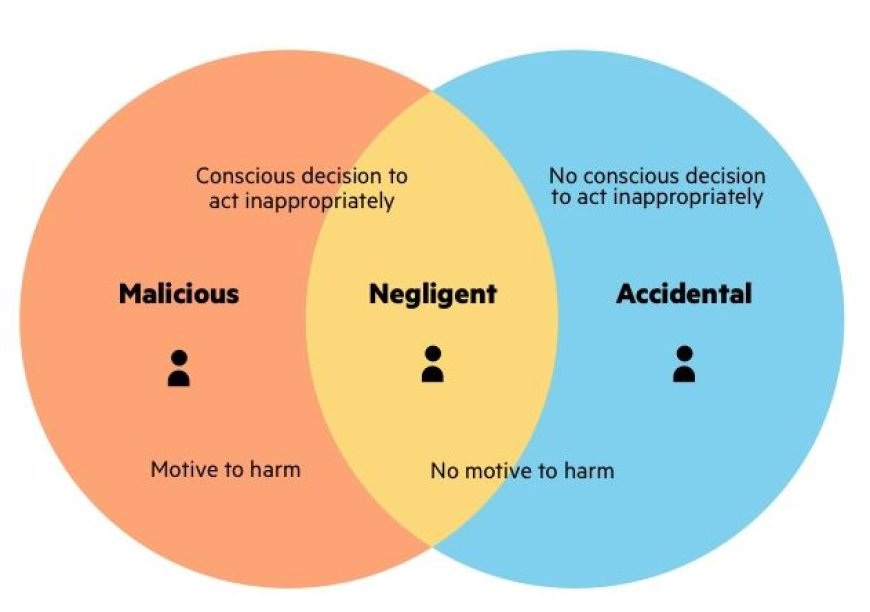
Cybersecurity isn’t just about firewalls and encryption, it’s also about people. In fact, one of the most overlooked and dangerous threats comes from within the organization: the insider threat.
These threats aren’t always malicious. Sometimes, it’s a well-meaning employee clicking a phishing link, reusing a password, or accidentally sharing sensitive files with the wrong person. Other times, it’s far more intentional - a disgruntled staff member stealing data or sabotaging systems.
Real-World Insider Incidents:
Tesla (2020): A former employee leaked confidential files and sabotaged internal systems after being fired.
Anthem (Health Insurance breach): Credential misuse by an internal user led to one of the largest health record breaches in U.S. history.
U.S. Government Contractors: Several high-profile leaks occurred because privileged insiders sold or leaked information.
How Do You Defend Against Insider Threats?
It starts with awareness and smart policies. Here are proven steps to reduce insider risk:
- Enforce Least Privilege Access: Give employees only the access they truly need.
- Conduct Regular Security Training: Educate staff on phishing, data handling, and secure password practices.
- Monitor Behavior with DLP and SIEM Tools: Watch for abnormal activities like mass downloads or off-hours logins.
- Use Exit Procedures for Offboarding: Disable accounts immediately when someone leaves the company.
- Create a Security-First Culture: Make cybersecurity everyone’s job, not just IT's.
Your employees are your first line of defense, but without training, they can also become your weakest point. Insider threats blend human error, privilege misuse, and sometimes intent - a dangerous combination if left unaddressed.
Building a strong defense doesn’t stop at the perimeter. It starts with the people behind the screens.
Social Snippet:
- Insider threats can be your biggest risk!
- Learn how to spot and
- Prevent security mistakes from within your organization.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0